Segmentation allows for targeting specific users and delivering the required training to them. Segmentation can be used in the campaign creation process, Step 2.
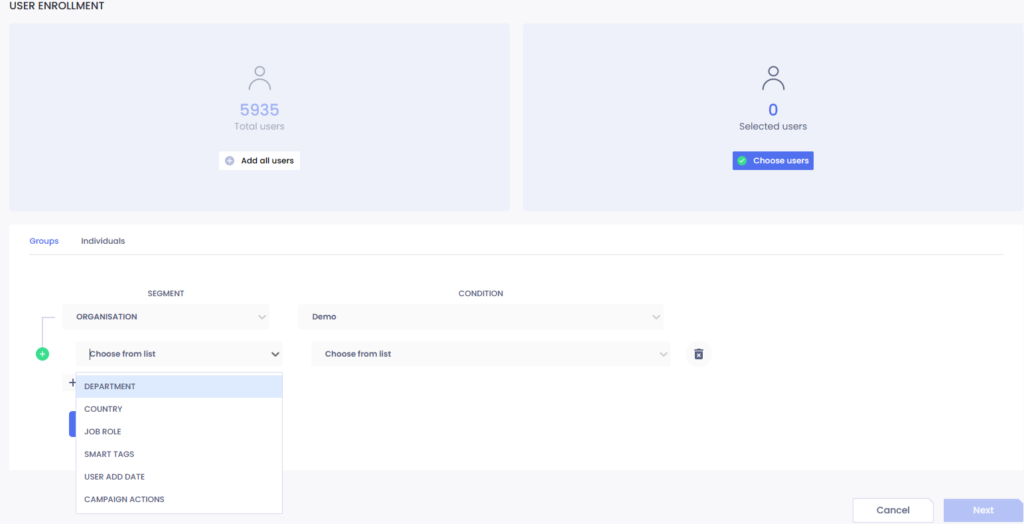
Available segmentation options are:
GENERAL
1. Organisation – ability to select specific users in the organisation.
2. Department – ability to select a specific department in the organisaiton.
3. Business unit – ability to select a specific business unit / division from within the organisation.
4. Group – ability to select a specific group of users. The group can have multiple users, across different organisations and departments.
5. Country – ability to select users in specific country.
6. Job role – ability to select users with specific job roles in the company.
7. User add date – ability to select users based on a specific date or period when they were onboarded in the system. The segment works with FROM & TO values in order to allow admins to specify the dates. The TO date can be left empty. This will allow for creation of ongoing campaign.
8. Campaign actions – allows the administrator to specify rules in relation to already created campaigns. For example:
- Training campaigns segment users that are:
- Not included in the campaign
- Have completed it
- Have not completed it
- Simulation campaigns segment users that are:
- Not included in the campaign
- Are compromised
- Reported
TRAINING
1. Low Knowledge – the system will select only those users who are below the satisfactory overall knowledge score.
2. Low Engagement – the system will select only those users who are below the satisfactory overall engagement score.
3. Trained – the system will select only those users who have been trained at least once in the last 6 months.
Trained user is a user who has completed at least one curriculum training session in the last 6 months.
4. Not trained – the system will select only those users who have not been trained in the last 6 months.
Not Trained user is a user who has not completed any curriculmn training in the last 6 months.
PHISHING
1. Repeat Clickers – the system will select only those users who have been identified as repeat-clickers based on their simulation performance.
2. Defenders – the system will select only those users who are identified as Defenders, typically reporting phishing/suspicious emails in simulations.
PSYCHOGRAPHIC SEGMENT
The system will segment users based on their psychographic performance. There are 16 psychographic segments. Each one has its own specifics, outlined below.
1. Gung-ho
Users of this type can pose a significant, unintentional, threat to the organization. They want to personally be involved in security but are burdened by inaccurate risk perception. This may propagate undesirable culture traits as they seek to take a leadership role. As they use workarounds their misplaced risk beliefs may result in options they believe to be safe but in fact create significant vulnerabilities.
2. Uncertain
Uncertain’ users are strongly motivated by security. However, they are unaware of the risks they may encounter, leading them to be unsure as to why certain policies may be in place, or unclear as to the consequences of any potential workarounds. While they may wish to play a role in creating a positive security culture the lack the knowledge leaves them uncertain of where to place their effort.
3. Naive
Naive users hold a generally positive outlook toward security but are more likely to contravene security policy when it negatively impacts their primary task. This is combined with misconceptions regarding what constitutes risky behavior. The risk for the organization created by this group is that they can adopt insecure behaviors, sometimes under the misguided assumption that they are acceptable.
4. Passive
Individuals in this group feel that security is necessary for the organization, although not something they themselves should have to put time in to. While they are aware of the policy, they are not always clear why it exists, leaving them following rules by rote. Lacking strong convictions, they are the group most susceptible to outside influences – if paired with ‘Champions’ they will pursue better habits.
5. Willing
Willing’ individuals have a desire to take part in the security processes, but have only a limited understanding of the risks. They do not fully grasp the causal relationship between their actions and the associated risks. This limits their ability to act securely in situations outside of those specifically covered by the policy. This also means they may lack the confidence to challenge non-compliance in their immediate environment.
6. Champion
Champions are ideal members of staff. They combine a high level of motivation regarding security with a good understanding of both the risks they are likely to face, and the implications of those risks. This makes them able to remain secure even in situations where no explicit policy exists, as well as carrying over good habits in to their personal lives. In addition, they will promote a positive culture around them, influencing others.
7. Follower
Individuals in this group will follow the prevailing security culture within the organization, without taking much initiative of their own. They understand enough of the risks to see security as important, but are not sufficiently invested in the process to pursue secure options if they come at too high a cost to themselves. Without the influence of ‘Champion’ individuals they can over time adopt insecure habits.
8. Expert
Expert users possess the same level of knowledge as ‘Champions’ but are not as motivated by either security, or the organization, or both. This means that whilst they are inclined to behave securely, their time and effort is more likely to be spent pursuing their own goals rather than seeking to promote a wider culture of security. As they pose no risk to the organization, there is no need to attempt to shift them to another category.
9. Reckless
Individuals in this category feel that security is more of a hindrance than a benefit, while also actively misunderstanding what constitutes risky behavior. This makes them likely to seek workarounds, which may introduce significant vulnerabilities to the system as they do not have the necessary knowledge to understand the possible consequences of their actions.
10. Apathetic
Apathetic individuals are primarily motivated to just keep their heads down and get their jobs done. They do not see the benefit of security, and are unaware of some of the risks, making them prone to committing errors, but do not hold any serious misconceptions about what constitutes insecure behavior. Of all the groups they are the least involved with the security process.
11. Abdicator
Abdicators represent a serious concern for any organization. Not only do they have active misconceptions about the level of risk associated with a given course of action, but they also do not see any value in organizational policy. They feel that security hampers their own goals and seek to go their own way more often than not. Where possible, the best way of dealing with such individuals is to remove them from the organization.
12. Rule Breaker
This group is highly dissatisfied with the current security policy, seeing it as negatively impacting their primary task. This may lead them to break the rules whenever they feel it would benefit their productivity. Alternatively, they may negatively influence security culture by being overly critical of certain policies. While they are not completely unaware of the risks, they do lack certain key pieces of information.
13. Excuse Maker
Excuse Makers feel that security is a hindrance to their primary task, despite understanding what risks are associated with noncompliance. They will circumvent the policy when it gets in the way of their goals, especially in environments when rule-breaking is the norm. They tend to excuse their rule-breaking by referring to the costs associated with compliance.
14. Circumventer
This category of individuals shares many characteristics with ‘Experts’. However, unlike experts they see security as a barrier to achievement and use their skills and knowledge to circumvent policy when it exceeds their limited tolerance. An organization that identifies such individuals in their staff population should assume that their current policy has not been effectively designed as it is forcing people to choose non-compliance.
15. Disaffected
This group feels strongly that security is a hindrance and rather than making excuses for their circumvention, they will feel fully justified in their non-compliant behavior. They lack the deep knowledge to circumvent security effectively but will instigate non-compliant habits and propagate those through the organization.
16. Shadow Agent
These users completely step outside the company policy. They have a full understanding of what constitutes secure and risky behavior and likely possess the technical skills to implement sophisticated workarounds. Members of this group are arguably the most dangerous as it will include both malicious insiders and those individuals that regard the organization as largely incapable of appropriate security policy.
BEHAVIOURS
1. Cloud Risk – the system will select users who indicate that they use cloud platforms extensively.
2. Security Measures Risk – the system will select users who indicate that the security measures in place are not effective.
3. Malware Risk – the system will select users who indicate malware could easily affect the company’s infrastructure.
4. Clear Desk Risk – the system will select users who indicate there is physical risk around the office (e.g. lack of ID Cards, paper left on printers, passwords left on sticky notes, etc).
5. Decreased Productivity – the system will select users who indicate that if they follow security policies that are in place, their productivity will be negatively impacted.
6. Low Self-Efficacy – the system will select users who do not fully understand how their individual actions in terms of behaving securely, could affect the entire company.