When running phishing campaigns, even after a successful manager’s test, you may sometimes notice false positive clicks.
During whitelisting, you must analyze (together with your IT/Security team) any additional security systems or configuration that your organization has implemented which may impact or interfere with email delivery and processing. Our whitelisting documentation covers the setup of such security systems, however some customers may have a different system in place which we are not aware of.
OutThink detects user clicks by monitoring a unique hyperlink for each user, which opens the campaign landing page URL. Once this URL is visited, we know the user has clicked. If you see an unusually high click rate, you should first analyze the ‘Link Scanner’ attribute included in the dashboard’s Export CSV feature.
If ‘Link Scanner’ has value TRUE, with associated ‘Link Scanner Timestamp’, this suggests a security tool has scanner and clicked the links in the simulation email. You can download the full CSV report from:
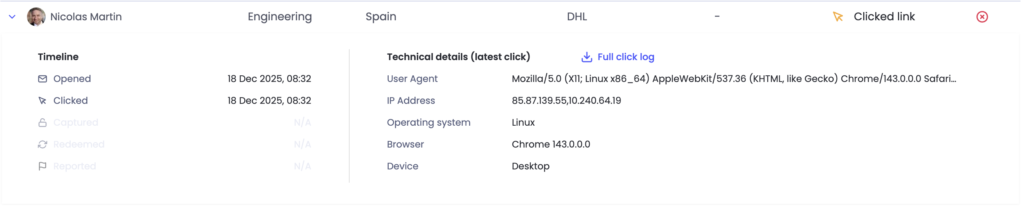
You can further analyze the record of a user who has Link Scanner = TRUE to determine which IPs have done the clicking – this will help you to understand which tool could be causing your false positives. To do this, click to expand the record of the user to see details of the timestamps for click events, the user agent, operating system, browser and device which initiated the click, and the associated IP address(es).
We have outlined below the most common reasons:
- EDR or antivirus software.
- Mail filters with security add-on packs that have their own whitelisting settings.
- Link preview functions as part of some devices (mostly mobile and tablet).
- Spam filter misconfiguration, or lack of whitelisting configuration.
- Device management systems (MDM) security options on mobile devices.
To solve False Positive clicks, you need to work with the team that has most in-depth understanding of your security infrastructure. We are happy to assist and help you to solve this problem.