This section offers a unique take on traditional analysis on simulation results. With Advanced Click Analysis the admin can gain insights into the question ‘why a user clicked’ and ‘who are my riskiest users’ at first glance. This empowers teams to take action beyond the traditional click rate percentage and protect the organisation.
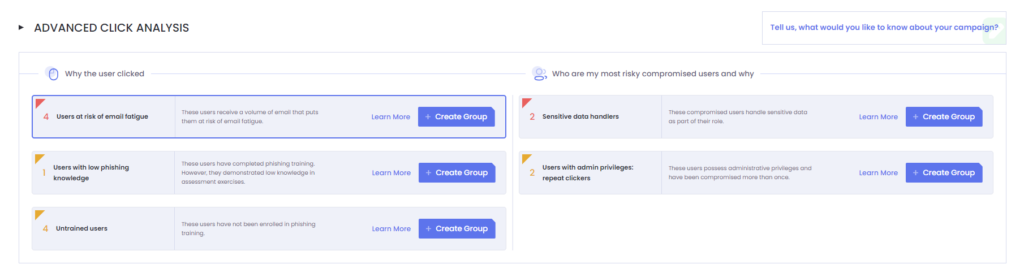
Why the user clicked?
These are some of the reasons why a user may have clicked that are available on the platform. Only the insights that have users considered are surfaced on the UI.
- Users who have never been trained against phishing attacks
These users have not been enrolled in a training campaign containing a phishing-related module. - Users who did not completed their training against phishing attacks
These users possibly have not even completed their assigned training that teaches again phishing attacks - Users with ‘low knowledge’ on phishing-related topics
These users have been trained against phishing attacks but have not proven a sufficient level of knowledge on the subject. - New Joiners
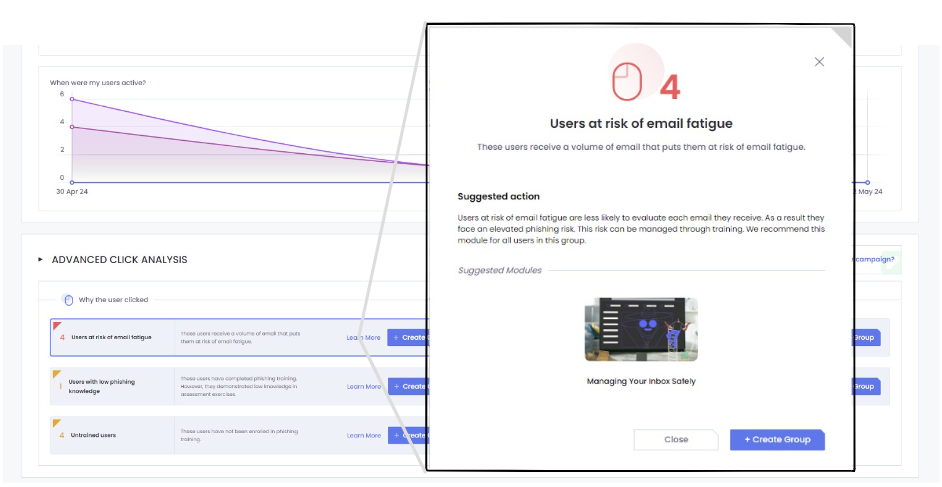
Users who have recently joined the organization, so they have a high volume of “onboarding” related activity and may have missed any recent relevant training on phishing. - Users with email fatigue
Users that receive high volume of emails in their inbox, these users tend to look at their emails quicker since they have to go through many of them a day. - Out of office users
Users that have opened the email whilst they had their ‘out of office’ notifications turned on. - Users that have not been targeted with simulations in the last 6 months
Users that may be caught by surprise since is not a habit to receive simulations. - Users with declared ‘productivity impact’
Users who declare that they have an impact on their productivity if they behave securely.
Who are my most risky users and why?
These insights offer a deeper dive into the compromised users. This section allows the admins to focus on the compromised users that present a higher risk to the organization.
- Users with administrator roles
These administrators may have clicked for the first time in their track record or they are ‘repeat clickers’. They will be surfaced as risky users with their respective recommended training options. - C-suite executives
Users compromised that belong to an executive position within the company. - Human Lateral Movement
Users that work closely with a compromised executive and can be at risk of being compromised by human lateral movement. - Sensitive Data
Users that declare to handle sensitive data in their day to day work.
Any surfaced insight in both of these sections, offer an explanation for the insight, a suggested pack of modules to train those people on and lastly to create a group.