Your phishing simulation CSV export now includes a User Agent column to help you better understand how simulation links were accessed.
This field provides insights into:
- Whether a real person clicked the link or it was automatically scanned.
- The type of device or browser used.
- Environments where phishing risks may be higher (e.g., mobile vs. desktop).
🔍 What is a User Agent?
A User Agent is a string sent by the browser, app, or system that clicked a phishing link. It identifies the software and device making the request.
Example:
sqlCopyEditMozilla/5.0 (iPhone; CPU iPhone OS 18_3_2 like Mac OS X) AppleWebKit/605.1.15 (KHTML, like Gecko) Mobile/15E148
🧩 Common User Agents and What They Mean
| User Agent Example | What It Means | What You Should Know |
|---|---|---|
python-requests/2.31.0 | Scripted click (bot, scanner) | Likely an automated email scanner — not a user click |
Mozilla/5.0 | Generic | Too vague — may be bot, proxy, or scanner |
Mozilla/5.0 (iPhone...) AppleWebKit... Mobile/... | Safari on iPhone | Real user clicked from mobile device |
Mozilla/5.0 (Windows NT 10.0; Win64; x64)... Chrome/... | Chrome on Windows PC | Real user clicked from desktop browser |
wv in string (e.g. SM-A325F; wv) | Android in-app WebView | Link clicked inside a mobile email app |
Outlook-iOS/... | Outlook mobile app | User clicked link in Outlook on iPhone |
curl/, wget/ | Command-line tool | Bot/script — not human interaction |
🧭 How to Interpret This in Your Reports
- Real user click: Comes from known browsers like Chrome, Safari, Firefox, with mobile or desktop identifiers.
- Automated scan: Comes from tools like
python-requests,curl, or empty/generic user agents. - In-app click: WebView or Outlook-iOS suggests the link was clicked inside an app.
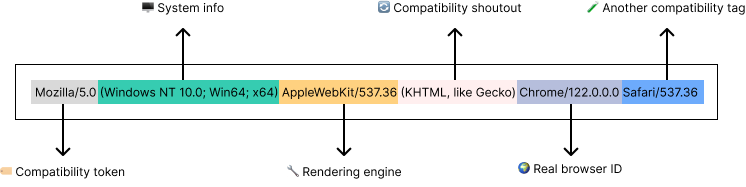
Or in plain English:
“Hey server, I’m a Chrome browser version 122, running on 64-bit Windows 10, using the WebKit engine (like Safari), and I’m compatible with older rendering engines too (KHTML/Gecko).”
Use this info to:
- Validate whether clicks are legitimate user interactions
- Spot false positives caused by scanning tools
- Understand how your employees engage with email (mobile vs. desktop)